Composable building blocks for secure, seamless digital experiences
Zero Trust unlocks the potential of truly digital experience but is too costly and complex to develop in house. Keychain Core gives your team the control and customizability you get with in-house development while enjoying the speed and ease of use of building blocks.
Trusted by leading companies across the globe





Your company’s and your customers’ digital experiences are encumbered.
You want to deliver new digital user experiences, but legacy tools hinder you from realizing this promise — encumbering you with designs that result in fragmented identity, siloed data, and entrusting centralized, unaccountable 3rd parties (network providers, cloud providers, and certificate authorities). A new paradigm is needed to your customers a truly seamless digital experience without entrusting security to unaccountable big tech.
The Zero Trust paradigm unlocks new experiences for your customers.
Zero Trust is a paradigm that aims to move the responsibility for identity and authenticity verification from the network level to the agent (application or server) level, where it should be. Zero Trust enables new patterns of computational flow for seamless end-user digital experiences.
Keychain Core provides you the missing pieces needed to delight them.
Cyber security is hard, and there’s a capability gap between the tools you need to build secure applications and the tools available (open-source or otherwise). Keychain Core provides to you the missing piece: self-sovereign Zero Trust capability wrapped into one, easy-to-install, beautifully architected,hermetically packaged software module that will help you deploy quickly and cost effectively.
' width='107' height='135' xlink:href='data:image/png%3bbase64%2ciVBORw0KGgoAAAANSUhEUgAAAEAAAABRCAYAAABi46DgAAAACXBIWXMAADLAAAAywAEoZFrbAAAQ0UlEQVR42uWcW2wbV3rHR6ZRbLPbhxZFulkkbV%2bCFgW6QPpWLIpuURRFH5ouFn1JFm3Toui2D33xtkC7aFeOnVi2dY3vl/gqr%2b04tmTdrTtFS6JIkZJJiTPD%2b31I3Tn3%2b/maMzOUmLiON1k7lpgBhMMxLJLf7/y/75w5539EEL/ktZTX9uE2lFFfCeXU8wsZpT%2bYUv55ISm/Xv0/8wnF5Y8rDd6oRMzFROvf5mISsacvetUglgtqA35NMtprSwVtviABxDcBqBWAYEpZDSSVc/MJ%2bY3a35uj5X1eWmywX0vELL0HQZArut2WtP24jTDafxRlgKWCpoTzqh7KqUYoZ0BsAyCQVEx/XL7hiyt/8NOB4e338NKSa4aULBCz1B6DsMTolgLwxYDRQJUNX2oLIMLoxlJBg3BeRaGcai6kVX0hrUJ0DcAfl/W5mDw5F5V%2b6I2I36q%2b1wwp7X8YkYiHy3ZqTC/vchihsmqnwIrhwi21qr/NKABU2dDJko4ijI52IGiwkFZRMKXqgZQK4QKAL6bAXFQqztLSgekl8deq7%2btLSIRnSbTqyWyYJ7w5iZgKibsQQEkjIoxJlFXBSQcjnOYA6FXDoMoGOBCgRgkIqyCYUlEgqRj%2bhALBtAlkGWCWkrLTpHTAs7wDYiYiNrjDgmsixFv37rCwuwAEyzqxXNat3l8q6%2b%2bkBAByxTCoVR3RqwZyIEANBHAgIAcC8sdl0xeTtYU0slQxQ0rF6Yh43bMkfq/6OQ%2bX5IbJkOCaXBSI8Uc2jIlHLxhGoKgS4bJKAIB1Hy5rw2kRYLms6%2bSKAdSqjpUAT4AANUpA/rgCvphszEUl3Z8wIJjGilDAsySNu0PCn9d%2b7sQC5xpf4Brs1ywxFuReUO%2bXNJwC1hdZLGuvhEra5vKqCUsrGlou6%2bgLQABHCcgXk3FNMGcp2ZghZVhI4zqBwB0SHkyGhB%2bOB7iXqp8/vsC5xgIVq06ML/LE6PzWVxe8n7GL34Iz9C2UtZaUDBAq6Xq4rGMIWAnwBSFADQQ0S8lohpSM6YhkBlIAM5QOk4%2bEwPgi3zYeZL9T/S5jQXb/iL%2byb9i3SYwGNohhPxAj/s3nC8BbVIkgY8/6AkX1tWBJY0NrCB6VNTNU0tEvCQFqIOCagKYjku5ZEk1v1AQMY3yB48eCXPNYYOu17TqxDsSwf9M1MLdm3T%2bY3ySGvBvPsQaUNKv4zTNqS1wGCJZ0bbGsw2JZQ6GSDs8BAvIsiYY7JGpTYRnmkwBjQbYyGqh0DPsrf1H9XosxRAz5NlwD3nXrfnBu/dkGPlNUiTnGnvZ6i%2bqrfkarLKyaEGA0FCzpaKFkQYBnCAFqIIBnSUTukIgmHwmaOySBLwEwGqhwI/6tB8P%2bzXdqv%2bugd33/4OxaQ9/MinXfP7v6rFLAzn0vo/4giGd2jGbOl1QUYDSsBHiOEKAGAq4J5vgCr48v8DBDIfAs6zDs3wwPzW28fWI80FD9vg%2b86/v6Zlb2VSH0z6wQ/dNfAsZUQSG8jE74CvYUdbaoDYU5gLmipvsZDeZLKnzFELASYHyBR2NBTh8NVAx3WIFp0oShuQ3/oHf9wMDs2vYDWP/Miqv3YXlfj6dkwen1lH/x4N0FxZ6fF5R9TvtngQ2A2aJmeBkN5ooqegEQwFECwioYC7IIQxiZ39IxCHdIgaG5dRiYXe3sm1n5bm08PZ6S6/4U03CnP2Pd33czT4fgKcjEQ0ZvsF8rowsVgJmCqs8WNeRlVKwEeIEQqkrANQGNzG8Zw/5NY2huA%2bHU6J9dRX3TKzd6H5bf6JkqbU%2b3u6eK%2b%2b9O5J4e/HhOwSlg9b47r/yVdw3AU1TM6aKCZgoqmi1qsHsgWErAENCwfxMNzW1oWAmTIQUGZteg11Me7fGU3up2F3%2b9Gt%2b9yfyTgx/J2fKfzKsWgMmCcjbAAkwVVN1TVMGBALsIAk4HqIGAawIa9K7rGMAD3xaMBnjomSoVut3FA3cm0t94qgLGsjaEkYz80nheSU2vALjzijlVUJGnqGAIsEshwMj8FjhKgEHvOhqYXTX7plf0/pk1mKYAut3F//nc4IdSMjGWV6yhbzQn/8THAUzkVX2yoCB3XsFKgD0IAWwIq1gJpa5x5jf/3%2bAHcjIx6qTASE755khOyU%2bWTRjLKeZEXoXJggJ7DALUKmHQuw49nnKly8387mPB92bsVZihnGJNe4ey8n9OVwBG8oo%2bmlcwBLTHIZgPfJtYCRu9D5nXHgeQlYmBnGINe305%2bZuDOZmaWAUYzinGSF5BozkZQ4A9DMEcnq/AwMzqZq%2bH%2be3HAHSnJWIgaw99/Vnljwayij6YU2AoK6PhnIJG8grscQjmSIDFStjonV599VPBd2Xs6W5fRnbZ6SDdcG8B1EDASoA9DsEcDbJYCdyAd/X3HlPA/Yxk9f79tPTdnoyE%2brIy9GdlNJBV0GBOrgcIeMIED3ybxuDcxvc/owCR6Enb8u9OS52jmwA9GVnry0oYAlYC1AEEa%2bo87N/Shn0bf7Id/EcpibiXtndq7qalN7oyMnSnZXQ/I6OejIzqCIL1EDUaqOjD/q0/tYK/lbRz/%2bOUZE187qakAwOrAF0Z2ehOS1UIUCcQ0MQjAcaCnDYaYO1l%2bBspibiTsiHcCCsNd1Kiv68McC8tG10ZGXWnJbifkaFOIOD1BDT5SMTp8CbRGbc3HW6nRJfTvt2/DnAnLep3UxK6l5aRnQ7PEQKjQqD0lS6qmLO0iRda/5H4aZy3ev%2bqkwY3k2K4iwH4KC0Zd9IiOBCgjiAga7WZNnE6/D0OGKeAy0mFd%2b6VAW4mReN2SkQfpSXkQIA6goAXWk1n8%2bUfrBQYdba6OhPC8L0VgJ%2bnJP1mUoJbKQkrAeoMAt58Mf0JBJ4l4e%2bI6wnBGvquJYRXrieEzRspGW4kRfTzlIRuJsV6hID3HYxgCmB6Wfwn4kpCsIa%2bqwmh5eN1gOsJQe9MihgCVgLUKQQN23hmSLnRkv6lhPDa5bjAXk8rcC0pmtcTAupMCPUKAe9Fati14qUlG8CHcaHl9hrA5bioXU2IcDUpousJAeoUAt6a12LrAHNRuZE4HxVevRDjK5dTMlxKiOhyXEBXEgKGAHUMQcNuNl9MOUici/FvfphR4UKMNy/GBXQpIcLluAB1DkFNVgDmE/L/EmdiwsSVIsD5uGBciPFwMS7A1wCClti0LHxniDNRnryY0eFcjDfPxwX4mkDQ4xuWmfMacYrm//pC1oCzMcE8FxPQ%2bbiAvgYQ9FQFYDGjXLFGgVNRfvrDPIKzMd44FxPgawBBT7OAleAAoPkfnM8acCbKG2djPHKUUM/poGd5gFBevbS9InQyyj/8sAAOBAHqHIIFYKmg3SZO0Jz1JHiC5t48k1TgVEwwTkd55CgB6hSCka5gb7M2RXSQFeJUTNjnQOi8vAIYgnYmJkAdQzAyHADJ6BOEE3gVwB%2beoDnudFzCENCZ%2blWCgVOALhuTOGgbQpSzngo7aO5nFxmAk1FePxUTwIEAdQbByArY4K2PVRVAtNO2F7eVYr/dQXPM6aSCIZiOEqDOIJh4Kkyt6IsWgA%2birNV2RO2C2E5zjeeKACdoTj8Z5aEOIZj0BkBkxchagbdTPHGWWSPaKVsFHST3cjvNrZ1MKhiC6UCAOoJg0puWyz21PQ/AENpJjmhzCmIbxf37qYwBHVHeOEFz6GSUR3sNgu/JEExyA7AS0o9tjraS7PZ5gDaKWz6dNW0IUR7qCIIFIFzWUp8Kvp2yR4RWylZBC8X9ZRvFoXaah44ohxwlQB1AMJfWsdVfe9ws2EZzxHGSIz6I8s6owHWdzgO007zeEeVhz0OoGrzLumX1fzwFKHtEaHFU0Exxf9waFaCN4lE7zaGOKI%2bVAHsQAvIxGppnVBS0laAvbTi5/tmrmeKsn/aofcKzmeK6TuUB2ihOb6d55ChhL0HAtl7kKMGcZ1Q1JgEEGW3xc72CzRTrqID9XmtMglaaR05N2CsQ0HRRBcfWa3oZVQ%2bsIqBEwOkQChaV158YfAvtpAJtPygdp9nOU0WAVorX2mgediuE8byKHDMnciBgb7PuW0EQ5gG8RZWZK6oHH2blbz2l9%2b1t8%2bOkrYJjEfY7zRQntMUlDMHcGR12FQRU42M03XlFnymbEOQApgtK%2bZN0aJzJSd/eOQZo24GeeB2ntpyWtR6UjpHsf58sALTQvN5K87CLICAHAvYxmmM5RfeUEfhZy9tcnioojVMF%2beXtE%2bxF1eVzzkI89WqOckRTpGK9Phhe%2bZVjJEu2pzQMwXAgwAuCgHbca5aFzxzOyfpEyYTZCuB0YMbzSuNkfifw6aLmmi3YJtBJDghvXn46gGMRjnifXieOkfaD0lGS/deOrAnNFGe00DxqpazC%2bFVDqDVumdjHOMIY4NnCjla5PJKTG0ezO1L3FFTXVF5usM89yNYhsIe/SPC11xHSPpj4XmTtV4%2bSLN2WVDEEs4Xm4SuEULXroPsZyezJyPpg0YCJTcvMWR7Myo0DqZ0en8irLndBaZjIyc7ZB/nLnRhrcmpBE8m67Lby4448wDGK1Y9THHKU8LzSoepUQXfTFgSzKyPrvQUDRjewj1FiejNSY39N4MM5xTWWs3vcE0fE6JcN/LMQmsgt602bIusvNZFsuCWpwjGSNZopDp4TBGzSQLdtJZjYuNWd12BoHaArLZU/SYfG%2bylxW%2boPcoprMG0HPpCRiQdZ5dkE7/T6p1RwhOS%2b35ox4SjJmcdIFjkQ4BlBQJ0JsepUMW8mRf3jvA59awB3UmL5bkps/Dglbfd4X1Zy9WeUht6043VOP6OgP3sdjbDE%2byRHtDgwjpBsd2vGgKMUZ2AITjp8WQjVrXl0zYZgdiYE/VZOg%2b41y7jF3E6KjbdS/Ms1znbXfcfdOsFsEV3PK/DP1oL3lu0j7IfCW68fIVnpWFTASkAOhC%2bjBFSzNW9ewTadrAofrwBOh/In6dB4I85tS/1uSnbdTdnPKXeTEnEvIxLdzzv4ndGAdVp7WHwvwp5tywM0Uax%2blOLgC0JANXuR2J%2bgX81ocKsMOB3KVxNC4%2bX4To/fSomuj1JCw92UvW5xJ8W/mD%2bk8H6EJQ47Kji8vPX770VYoYkWMATTUQJ8DoTq8hqyN18EvCFrXM7q0FkCnA6lSwmh8VJsJ/DOlOS66bjZzq4BcSv%2bggLfSQWeaAyUicMUb6ngUIQ911oAOEJyWhPFwedAQDUQjFMxQce70pfyCKdD8nyMf/dclPut6udcS4quq3F7YeZKnCduJMVta%2b8LvQ4v2bXg0LI9LL67vPk7hyNssSkmYQimAwFqIKCaZwejI8rr57IGXCxa23CPTkf5H/14dOcPpHwYF11X4kLDNSfYK7sh6CdCiFSsB6VDZOUnrQzAexFOO0JyOB1QtTA6Q6TRSvHGybQBZ4sAH9Dc4gmae%2bsAZy/KXErzxIW4sO9CzO7xk0sacXE3Bv6pB6WgQLxL2iAORja/cShS8TUlNQzBqIGAh0i9I6PDyTxeT%2bDCbRT39n%2b5k9vvczom7D8fE4gLMZ44GeOxc404u9uDd3rdat%2bNVKxacHC58jdNKR0Ok6zqQNBb0zpY02aSfdRMsz%2bq/X28NX86bp9TPBUTrJ89d2EIPwtvEVdWbSkfXK4Mt68BNCVVaMlZhXHxKMm%2b9X6f5Kww8UQbxbs6nBWn6lL8nr0anVrQuFxpsNut3zi4XPmXQ5HK%2bcMR9m//bVnb/rMWzTS3v7obfZzmiFb6xQf/f2ZZ4Sv9N2QpAAAAAElFTkSuQmCC' /%3e%3c/svg%3e) Self-sovereign Identity
Self-sovereign Identity
- Each of your customers’ devices is enabled to manage its own cryptographic keys.
' width='107' height='136' xlink:href='data:image/png%3bbase64%2ciVBORw0KGgoAAAANSUhEUgAAAEAAAABRCAYAAABi46DgAAAACXBIWXMAADLAAAAywAEoZFrbAAARSklEQVR42t2cWWwjyXnHW%2bTYm8CwXwzHsWMYCew4gIMcxjovThAjzlNgGBvAyAUEyUMAY5M8xA95SOwghneCZGdndjSSRppDc2jn0GhmZ6XR6KakoSSKlCiRkqhbw1vsrqpu3mSz2exu1hdXs8XV7nhndzU6t16qSxDY/f36/6%2bqrv6qOe4Fy1JMtbF6MVr%2bTX9Uve6LqI/nQ%2bV/8AbV39r5H2%2bwfGp2S2mYWS%2bZ7dlNhTvxZRVp3GK80sCOAwnt60vxymqsALApAawhgPlQGc0F1SbvVvmb74JQbZ4Nxe7eqIHwbCmcZ/0Ewlgnhlkv89ops05op%2bMywGKsoi5EVd0fqVQX4wZsJQHmgqrmfVq%2bPrNV%2bsbu3/BslO3Ta4oJcPqkQYhkDW5F0MyLX0blT68K2hoLNrCtGYuxCixEVcog%2bMKq5o9UYJ0AeJ%2bWq7NbSqt7Q/nz6Q35V3d%2ba3pNOeVaqSnCFSxxrtVjDmNd0mo11uysXsPaj3gFYFXQtRVeo4FtjdYhRCvgC6vV%2bVBZnw%2bpsIYZiAp4NhSvZ1151bla%2bpWd351aLZ2aXCk1uBZkbsqCMLV8TGFsiLpZb6WMlzaIHg5lmO%2b16qqggwUBdimB%2bsIq6xPoXFDVvU/LsBADWEUA7nUlNL1W%2bpepZeWlOog1pWEiINufLBfM9kSgeLyCX5E0blM07BaIv4/mATaIXl3HOl1DGrUgwC4I8D4IlNlhZlPR/BGAAA8wvVoKTa0o/zq5UvqDnfNMBko255Jsm1iUzbZzST764ANimVuXKuaxP5m2rYvaeKwIsCkaxgbR6TrWmRLgAyDA%2byDAzKZieDbK%2bnyYmqqYWinlp5ZLdycC8p/unPPJcqnhyULB7vDnzfbYQoEb8xeOBsCipHFrUq3zWxUrX1uTtPJm0oANSaebosGUAB8RAlgQ6OxWGTwbZcO9rhjuddUE4d7QYCIg9zuX5O/sPv/4QsE%2b5suZ5x%2bzgBxaWSBqbegTK%2bbQtyJW2uMVgDVJ0zckfa8Q2OhAZzYVBoG61xXqWi3pUysKnQ8zEAY4l%2bTu8YXCKw5f/gs71zLmz59yzOUahj0Zsz0ylz14AF6scAGpNusLSOo3A5KqrqZ0WJG06pqk0XXRhAB7hAC7IIBrtUSnVhR9crlUnQuxzlKH8YXC5pi/8N9j89kv7lyTYz5nH/ambYPeNDczWussh2czB9TzSxq3KFrTXqKeiWoAAamirUgVBoGuSRrsIwRqQYDJ5ZI%2bEShVXasVYKoY8%2bdTo77c6WFvrq6I6ZUSN%2bRN2wdmkmZ7p963MkcUzofKNSUIyucWSNm/lqWwJKrVgKTSZdGEAPsIAXZBoJPLJcogOJdkbXK5DLNBgFFfLjMyl/3ZsDf9x/XZZUDhBmeS9oHpJNc7IZl/e%2bzaJxjzRDG97yPK32zKAAtErS4SlS6JKgQkFQ4IArMD7ILA%2boTq%2bEJRnwgo4NkEGJnLasPe9PDQbPqHu693YEay9blFs8Psn5G4vmlxb4G7cZGbJ%2bXdINxrRQC/WNYXSBkWiQqHBAEsCNS5JLM%2boTrmz%2bujvjxMrWowuVKBodmUd2Am%2bcpjR9a%2bc719btH22EVM6/a7JO6xC398CLNEtlv1K6slgHlR0X1imUGgRwABdkGgY/48HfXlDMd81phcVsG5VIYBT3Kx3y39c59H/NpODI9d5FTvFG7onkiY7V63yPU4E88P3EWKnAfL3EK6NgTOENkbKALMkZIxLyrURxQGAY4IAuyCwPoEyiAMezPGkyUFRubz0O%2bW1L5p8WqvC/9OfeSYkxt6JpBpjUcTH6KGCZzj3ES2WVb4hofIBW%2byDLOkVJ0TS3ReVOAYQaAWBGAQhmZT1cGZFEwsV6BvWqz0TuFrvVP4t3diezSFG54bvJPUppvTYtGU/zQp/teyCuAhsj4jlmBWLNE5sQTHCALsKOEXowODQIdmU3TAk9QYiCdLZeidwtqjSfSwxyl8o6YA9HwIU6Rg/sMULnzeRYqZmXQZ3ESueohMZ0SZQYBjCgF2QWB9QrXfLel90xI4fEV4NIlozwT/V88NfhIXuUmSN%2b/%2bJCn8z4IK4BKL%2bjQpUrcoU48owwmCwJTA%2bgTaNy2qT5ZU6J1Ewx8Y/AjJck6SN%2b/%2bOMp93knyIU9WhSlSqLrEIkyTIrhFGU4QBNgFwXDMF5gdFjpHE59%2bJngHSdeevEjOvPvjOPdP7lwFnGLemBQLDAJ1iYWTDMEYW5BZx%2bjrcYY/9QyARyTDOUiBGydZs/cfJbnuGbkKT0hed4p5OknyDAKcYAjG%2bGIJ%2bt2i/53h6LMABkmac%2bDaTMpBst9xpkswSnJ0HOfoE5KnTjEPJxyC4QyYk6X5O2PE/p7g%2b0mq9khp3f0Rkumflg1wkKw%2bSnJgQYATDsFwBhSmhLV%2bj/jZZxQwQNK2mhIyvztEMsaImGUAqANn6SjJMghwwiFUnyzKTAnC4Ez6q%2b8Jvg8nOZf14DNAUucc6SIMkUx1mGSog2TBgbPwCYBQZQoYmcsmhr3p36gH30MkdvctKyQ/009SvCNThEGSrg6RDAyTjAmAgTjhEKpsTWHUl%2bNHvNmvmAG/g2vPyr0kaT7zPyapV8flCvSTtD5A0gwCfQ%2bEk62E6tRKhSkh7pjPftkMvFPYZgowJz7dGL/0CCdDQ9ki9OGU0U/S1IIAdQgn2w6mAsYXCvkxX7724vYxKTMA5pDQTaRXR8saPMJJrZekGATaT9LwDISTa4faytJi0Rj3F/6I60KE6xUx9xAnGyw7dA8WZOghkvEIJ2kvSTII8IEQTp4SzMVWZ0DWnEull00FPEDYZtXffohEvZskoZtItIdI9BFOwnMhnDw7UNeqqQRtYkl%2bmesSCPcQixYAcmlQUYFBeAdLtJtITAnwoRD2aAfv0UCg02sKew2nTy7L3%2ba6UG1l5B4iX%2b9CxHiARXgbE/oQifAOluBjQcAnAgJlIFyrJdW1In%2bL60TY7Pw6Ee7olUtwHxH9ASZ7g0BOBAQGwGBvpqfXSt8z%2b4C7gvCFuwjxD9JpuIdI9T4i9AEyIcCelHD87aCti8ASNX5gAriN0A/uZ9JwFyOjE2F6DxF6HxN4IQjHVwnsrbTG0nY8G%2bXvmwBuIWHuQT4HdxAy7mIEnRjDPUzghSAcbztoLJttdkv5PteBEj%2b8l8/ALSwYt5FA7yBE9w3C8bWDxpK6vE/Lf8HdQPzkvUIWOpCg38IC3MYC3MEI9hXC8VOCviECeIPlH3PXUWL7LQnDTcRXO7BA3zoICMfFDvE6BBPAL5TwE%2b4a2n69SynADczrNxFPO9ABQTgOdkjUIejMAr6w%2bh/c1cT2l6%2bh7URHEsMNxFdvYh4OFAI%2bFhD0pykAf1T9T3MUaEfb/9ilynAdJ7QbmIeb2FQCfGLtkND0YBpgMar%2buwmgRYh/ql3Ynr6VTTIIxg10wBCO3g6GCSBeOcddFeLmVPgqH/vuDQnBNZSoXscJegMlqGUH%2bATawWAWCCQqXdylRITrSBHzgeiKEB%2b4nc8wCPp1nIAbKAEHCuHo7GCE0gDLvHbHtMBlPma36u%2b1Ex7a0Ta9hhLUUgIcuBIO3w5GOMMSvLW7bBjkfh7wc9dE3lTBZSE%2b%2bFY%2bBe3Ctn4NJeDQIByuEoxIzkzwvs1dSkS5B3KOuyzEzEWRS3zsz66nMFxBcbpLCZ80OxjRHMA61rpMCzAIbfEIdy0jmCq4JMRud%2bRTcEWI6%2b1oGw4NwuHZocpS/DeIHqgDYKXNUkEbin31EorpV/A2g0AtCHBoEA5eCdVgxsxyX66/GWIQmsUY18bHTQitQuynN3JJuIzihgWBHhqEg7aDqJkANkRLAbtLCx81bXAhGv5MmxCLtKcQg1C9IsThUCEcpB1ErbqVAVgXteX3BN8qxDjLAvZaO/pvN4tpuITi%2bmUUp58gO1Q32TYfsbLwrAISUe6ipYKmePRzrUI0dDWF4ZIQNywIcKgQDsYOdDWpwYpYyT0DoJWvdYgXhaipgot89MfXC0loQzH9EorDkUHYHzvQdyFUjPV0FX5pllgbitX7guZ49LMXhWjsSgpBmxAzjgzC3u1ArbReakFgWe7aUxkgIKrrvxRAy3aUa4qGuRYcNUeEZiHy15fTCFqFaLUNxeglIU4vozicADvQWWJltBKl6iOKvpTSIaQCLIpqPCCpf/LcZMnz8afcFSKYx80oMt2ekxgEow3F4EghvM8OE89CoCYEltFK5OosKen%2btAYbCjA7iH5SPu3H5S8%2bN/gWa3LUxEdMFVzgwy83C1G1Fcd3KwH2DAHtrx0mail8tJbHaCZzVt1E1r1pFVbKALNEFr1EPj2P5S/Vd75bW4A%2bsAwJwJ2JRrmLuAahSYh0tBeScFGI6q0oBi8MYf/sYKbwmUoQ89UpUtA96TIsKQBuUpQ8RH5tdlfgC2LZ7sflhg/dKNGEIpx1900AjXzo95qFiNaCYgwCbUVRsOywRwj4RSFQyw4sj7HKkjldaQV8CsAkKUguUnjNhQv1wOdExe4jpYZ5XNv8OY8/wt7k84ko15jY4lrItqWC8M2rxSS0CFHdgkBfDMLHtgMdxGbOEh2p2aHqwFndmZJhVgF4QnLiBMmfduJsPXCPKNtniFz71gEFbgbvYT9yIx%2b0VBD8/SYhXGnBMQaBXkT7oYSPbAfaj62cJZyuDuGMPpYsgLtUZSCkUZx9bRy9G7hLLNhduJby7yJ5ziXJewv%2bAh%2bqWcLqCxqF8M0rRQmahYjegqKHYQdaS9dJQR8xIegjqTxMlnQYwmlpGGdec%2bBMPXCnmLdPklyDG9c2XE/hfdhrzCA0okiDBeDXGlGEtKZ4BsFoQfuohPfagVqZKjvpOlqfmIYnig79OCUO4NTpAZz89fqWWpK1j%2bPa3uIzAJwT7%2bOW2mYxXrMCCpu5hOeF8E/a8iI0oYjejCJgQYB9tAN9G4s7EPRuIlXHVB0ekaTSi5M/78PSl97d35CzO3DaDHwEp1mbG8X7vJ%2b4MRHkLqAIdzYRNNs/XZi1vSmE51qzGJqEiGFBgBeEQDsxppYSWJKGziAMymXoFs3Erc4eLP3hrrxm%2byBONThwbZfoEN7nLbMfVN4UQuaD0jk%2b9HctGQEaUaTaJERosxChe4KABHobC/QORvQuQrQTYa0LE%2biTFXhARHgbka6HSKx/XIFltPZbaX07Oc6HVq6keO5MfMs8/llgxfamEJo3IQhhowlFoBl9bAi0A1sQkKAzCD2lUs0OiNy7j3D9jvdgydZDJFsto1ViKb1c92EGz8qOBc5ZKjjLh/62OSvAeRQ2GoUwbUIR%2bhHtsLPQSm8iXmcQ3pYLcIdglqnSeRcJ39o559tYtD9Eoq1HTFq5zdLRfkrjHB/k3th%2bah6/FliynRVC/pYcgvNC2GhEEXgOBLprZYktr5kvY7vkPHQQpgK%2b6xbi61K/h7H9PiK2hwlitu8LmDsWZUcFZ4Wg3aq/e16KwZtCyDgvhKmlBHgPBKE%2bY2QQdAbhrpyv2QEl7t1EibrUb2PedhchU%2bp3kcDdlgh377gEX4fAB7lzOMS9IdRmiGeF4MM2JckgaOdRGHZB2OkT2DxBZxA6ihlgS%2b5XhXhnuxCvS70DC/ZbiLd1IrKTvXb8vyr1Bh8yAZzhQy%2bfFYKlN3GYQaDnkaUEwbSDxiBcL6ahDceZHbouC7G61K%2bhhP0m4m23eN5s3xT4k/FJrbNCbYp8FtWscIYP/m9LUYRzKFS27KA3ojC9KqcsO0TuXUTRutSvCHFbO6o9ZLUL21xbOsRdRyck%2bHcVEORe55%2baY/L/JTa/coYP5trUDFzIJKBNlqARR%2bACCnc2oXBd6pdR3H4JxWw3rDt9BcVP7mf13rBU8Ibw1LyTr/NP//IMHxw/KwR954TQ7fMoVL/jzULU3irEbM3IWnm26qMs/w%2bRc/baevBkzwAAAABJRU5ErkJggg==' /%3e%3c/svg%3e) Data Security
Data Security
- Your data is digitally signed and encrypted at rest and in-flight, retaining data ownership for you.
' width='107' height='135' xlink:href='data:image/png%3bbase64%2ciVBORw0KGgoAAAANSUhEUgAAAEAAAABRCAYAAABi46DgAAAACXBIWXMAADLAAAAywAEoZFrbAAAPzElEQVR42uWcS4wkR1rHo7taaPEuB1bI2CsbuFggJFYyEge0IBYhhDhgVisu9gpYEAIuXLxwQAJ6OWMhTuzuASHWPiCB7PV4Xt09j55%2bv99dWVWZle93ZuX7UZWP%2bJjIzOrpYXbH9nrG011OqRVZo%2bmq%2bv/i/32REfFFI/QJr0NhNE3aA3744h43/N4OO7y6wwz/YpcZvTL%2bP5u9tLXVS6fWuwla66TVv613U3Spr7aWowMxmyL3x0r%2b8oGQbQshQNcCONUAtpnU3GKG393qDV89/3vr3WR6rZNWv7fWTdA6dQlBdPSyao/lbIa0R3L2t2IEcCBkw31%2blO9xo2Kfz6FjAmzRw3KrN3xnq5f%2b8ls6d/Yea1TaWm0nFYjVywahYxWorebVfTKMp06UfJO2AY6kUXEgZLDPj/AeNyp3%2bsN8pz8EygDY7KX5Rje5u9ZJv77eTb8wfq/VdjKzcpqg5ZMawvLpBYfR07MmBLIWaSktf0OKAU6UPD%2bWM3wkjfA5CLDTH%2bJtJs23mSEcSgAb3RTWqFRZo9I3l9rpT43fd%2bPUQUsnSZVPlg9jtNz30dJxejEBtC1Aeyd69ZrSiyPWAzhVs%2bJEyaGBAOcgYOKCbSbFW/Sw2OwNYadfwIkGsNpOhJV28ubq6QMQS8fx1L2juLV4FFWv7x3HFwsAbYxQ18yr3u%2ba%2bTdJ71N6UbS1HJ%2bqGW4gwDkI0EDADQS82UvLjW6S7bAYDmWAldNEWT5Jvr90knxl/Dn3DuKpxcOodfcgQncOawh3D58xDEYfop6eo1%2bDTu0GI5tTEoCOWeSUXkBby4kT4EdAgHNOIBBgo5sUa1Sab9I57HLEEUNYOk5u3zuKf%2bf8597ZC1p39sMqYd7dD9GtvfAZ9b42QrRRD320kb3Y0zOHNkvoGjnumAX%2bGBCggYCbnFCutpNi5TSBXZYkTAyLh9HNxYPo64uH0XPjz7%2b9F7Ru7frTzT26teN9ir2vDWsI%2bmimyQVvmSOAnp7lPSMnEIgT4GNCgBpCQiDg1XaCV07jYvkkKXdY4ogc7h5EO3f2w3%2b9sxd8afxdbu36M/Pb3vTClosWdgZofhvQwrb7dAH01REJgYo%2bYwxfpvWRz1ol0Mao7OkZ7uqfCAKsd84gwMppjJdPknzpOC7XOiVsswC398Lw1l7wL7d3vZfH3%2bl/Tgo0t%2bW2bmwNqtdzOw6a23Ceagi0mlzwljUEoLVRRusZgYB7egZPAQJeOo6LxcM4u3eUwnYf4NZu4C3seP82v%2b3/7tmzxGGMbm4OWtc3ahA3NgdPVjirJojRRlONE15itKHHWQXQ%2bhDT2gg3EOAJQoBzEGDpOMaLhzG%2bexBli4cJbDIACzt%2bML/l3pzbcr55/rte37Bnrq9ZU1fXzOr1tXXrSUEYVrHPasOviXYJjDYsGW2IaX1InABPEQKcg0ByQnl7L8xv74WwSmFYOslhbss5urHhvPH9vf7UGYg1a/rqmlmF7LU1E32waqBrqz8GDEGJiWjUk8KxG26YIUBfS3NGGxIQ8EQgsB8ZAnECyQn41m6QL%2bx4xeLREFbaJdzYGGxdX7ffvL5mn03Arq4arSsr%2bvQHy3oF54Nl46OL55X6wYNT60dUVk1%2bW3MA%2bmpasFpKIOBnAAEaJ2Diglu7PiYQ5rfdnIBYPBzCjQ0brq2Zb19dM758Xs%2bVZb31g3vq1PsLWvX6/XvaR3FAhGitnr5yarJg%2bgCskuSsmuK%2bmhAI8AwhjJ0ACzsent92i7ktp7ixMcAkNK6tmfjqivHOlRX91avLxtnj9nv3lJl3F%2bUPFy/KEeLlqOp9Xo5%2bX7NL4NS4ZNUEs0qCWTWFiwOhcgKBgOe2HHxjY5ARJ9w9HMK1NQuuLOsLV5b0139wT/3psb7HQpCUcBwG0037nUEAwCtxzqkJsGpMIMAFgkDCAc5BIDkBX1%2b3cwLg5qYLCzshvL%2bkye8tKm/%2b713hcx/ugCYHyHL6nCBHrGpmwMlxySsx5tSYQIALCgHmt11onADX1218bc0sP1gx8qurFqxQAO8tKv/wePFmgEQpnKlDIfyWHwHwcpjzSoQ5OSZOgE8Dwu6ThQA1BJM4QXv3tvozP1S8LPpEfHWvSOHnRSmQNGMIghSWghwBr0RwySDAeSdcX7fh/SXde3dR/YVHxCuSX%2bcAKagee0Ux%2bDvPAxClMBflkEDAvBxeZgjlzU2HOGFwZVl9%2bVEAgosUyauGPV1yPy9JPmVZOYhiUIhSiBsIcIkhlHPbHlxbNZ0rS9rPPQJA5T0SAtNNKPyqLPq5JPkgiT4WxQCLUgiXHEI5v%2bMTJwyurJgvPSReE%2bo5tSx4rRqA907gAYwhiCL5CeCSQygXdnzihOD6uvWLjzpA8KYbJ3xZETysiD5Igo9l0ccTAoE8MBEnFDc3na8%2b7ADeQbLgNgCctyMXQBG8TBY9kASPOAEuP4SgenSe33az%2bS3nN8/E6/wAqYI71YTCq5rggiI4WOFdTJwwQRCqSdTCjpfPb3u/VYvn7LEDZpr2zcDKQBXc4hwEmBAI1XT61m6Q3doN6mV4i7ORLtQQCuhM6fxgyzeGoPFOoQpEvAMKTxwxERBwDSEmbngNmazZuGDQato3EqcAnR/kGjfAGu9gtQ6HSYFAFlWqxdY7%2b8GfIZMzkcU7qE%2bpNQjWPvK0GDR%2bUOj8ABoIMEEQ8Hi1%2be5h/CfIZkxksnbV%2byZrfzMyUtBZq9A5G2v8ADcQYIIgkIXWcoNsvhwlf4pMzkK/8cV62muy1lxiDsHg7FxnbdA5mzgBJgwC2Xwpt2hMwuGPkcVa1dBnsdaLJms6NjcAk7WwwdlYZ61JhED2HQqy87R8Ev85svpGNfTZffOt3M6I%2bNzsW6QlToAJhZC1DbIrHc%2biWrz%2bss0YvssPwOybpcma2OybkwqB7EVmlAmwRiUNAEZ/q7BHYDNGZhHhfRObbNVOIgSyK511LID1TjqL3L7x0oDRPY%2bzwe7r2GYMbDFj8RMLIevZpFwn%2bTZyGP21UBiATeulzejY7uvECTDhEEa0UxVu/SNyaPXOSA1gwOjFgCbidfgMQMi6NinhS/8duT21HQsDGNBaOWB0%2bIxAyElB5zaT/hdyaOUPUtEBhwCgNTxgdPwZgJDTAyBO%2bM9qFHBoZWUke%2bDQauHQGnwGIOSMA7DHNQDcnvK1VByA2yMAVNw4YZLDISe1jfv88D/OVoTcnrKcKX4DQYMJh1ABOBBG/428rlLNBN2u8lrEmuDSSuH2VNw4ASYUQkFywJGU3UMBrSO3K1cLoV5PfRvMlEDIXFqFCYZQ9F0gTriDauFKA0D5Fa%2bnBAGjEwh4gp1QkBA4UfK7pNfHEKpZoddV/glrIckFOXFBAwEmDELB%2bwBtLbs1Fo/8rlKtCwQd%2bQWvq6gxyQc9tWycABMGoSQOaOv5fg2ArouFgp5aJUS/q8yWqg9uV8m9ngoTCKHsO1WVu1APgZSEwMmQ15EqF3gd8Xm/K1sxaxAIpVtDgAmCULIOQNcs2AfPAZSEXEpE/jghduS/yYQBeD2lcLt1QpwgCCU7AOgZOffI5qhHyYiBvere78gnuehUELxeJX5SIJQccYCRsw%2bJJy6oRwKpckHQlX/P70rY78oEAm6cMAnhUHIDDD0jEx9xgNuVKxARXY8Kfld6t5Rd8LpyXrng8kM4K/DuGaPyEQBBR27sX7vA70i/HvYU8DuVE3DjBLiEEEhZb/2jj4gTcm4A8EOrxIgD/K6E4q585gIsuwRC3kCASwaBlPXixgmkyn1kpgCMPtp/bK1gcJYLxK/EtApE/DknXAYIuKpqVRLcV9Oyrya5YBVgJ0T88JDRs1d%2bpPiQbkKh10DoiG%2bD6hMIGUmKFxgCboo5cQ0hIbXNuWTmYEVVmb/aV9NvM1ryhcf2/nhECDvidN1KXwo6YhQzGhFfNk6ACwYBkzrGppiz5OQ4l40R2CEAp8T6/XCYZdT0hXNHgKYfHwJjCJQ4U7fS34Psgd%2bV8oC44OJAwFINgdQxloIU5ooxAlLcTYRzSjzLydHzD06/pC26OQX3oVdIiSig6uHSb3M/EVJiO%2bNMAqFoIMAzgoClqnZpXL0WlKIY5Ko%2bBNcHEg6qIIezrBKfE560mObsQ6Am5BzEhwMIOhIKTjukbdWuEP4aiw4EHbEI6ock/AwgnCvc8ktSx6hpCdQlvYF%2bPxfM8lJwZnVeTVqcHNWHPuQIsVqMOOljHswO2/2mpX8ypIROxhoEQhl0JfgUIdTlOnxVuFUqgpcbagy%2bi0k46PedMCuK7vMPDnyELVaJp7im8HvcfuwrpLimFVpN%2b1cguxBQYh50RNw44WmFw7hSpSrV0XinVAU3N5UQQgeDIrjq/ZCYFTn/nPCgJUj1WePEDH584Q%2bFQptFIcVPNffPRZRwlLE6gVAEHRGeEgRSpIEbJ5SkcMuSA4gGBQkH/X44zCq8e2Z1SQxaYlPoLUoekqUnJL7udb5qI0qsXBC1xa%2bCYENIwoAScQMBnhAE3BRpkEqVUmetfCD7ENsZCQVd5QazGvfA6orotUTen5IUtwHxlM4RRx0JRW0OuXR99i5qC%2b9hwSIQigYC/gQQxlvz2KodUJp9K3dED1I7A521Va0Sbj3/oLLdaSlNdWuWJEjinvIB6rNc0Oanm/aVqC0kSVcmEPAncAKut%2bYN4oTSYszcFRwYWkMw%2b5ZusNaswVkvnKtpbqmcU5f1sg7SJOfpiz9zASWMe78KhbjNfwckFyJKzEMi/uNBwOO9yKY%2bIfcFB0ZGClbf0M2%2bMWvRD3rc4AYtjbOnNLY%2bAqtxFnomF3k4iimhckFMCb8Ut4Uo6UgEQtk4AR4DYby8hl1aI7vSxYDWilh0IddjAkOziHBGPxNO6hgNrq5mw2zw7ISPr1FbQRZFobRJiDElfBcUD6K2kEWUCI%2bBgM9BKFxayYeyB8NqZ1rrD2jtn%2b2e%2brMPhFstkzEr4SZjIatvPnvxDz8X1MNi1OZ/PqJ4ZUQrBELZQIBzEPC5uQNZX8xHogulGoBLqwduT/uGvbV89v5232hZjDFl0fWmjUVr6MJdYwgxxc80ueBboAUQtfksagskHPA4MYZV70sFEZ/xNpBptddT9r2e%2bjoY9aKM27fQgNGn77ugggqiczGFPzxlplHarpNi3hY%2bF7e5zZLVCYQios4gkCEyL3gLyKpS0JGP/K78RoofrEg7tDozYHRkMjpyugpyGf3ii29iv/5zWm2%2bzgWn3B8CZ0BE8aMKQlvIS94CkKvJ00HYEb/x0BJ8T2mNd6VcWkH%2bZRD9/6%2bUElB4zCJI6wMXySk/B3YKxAkgORBRwn7UEV9v50u10BOBLLu3fFppIMjoUl/hcZMLTuuEmHaEL8an3F/Gbf57EcX/EZwwUw%2bm1uJM0Fea9UbhbAX6WV7/B1Jpz98wTkW8AAAAAElFTkSuQmCC' /%3e%3c/svg%3e) Verifiable Credentials
Verifiable Credentials
- Any actor in your system may create digitally signed attributes pertaining to other actors. For example, “is over 21 years of age”, “is a person”, or “is authorized to receive certain data”.
' width='107' height='135' xlink:href='data:image/png%3bbase64%2ciVBORw0KGgoAAAANSUhEUgAAAEAAAABRCAYAAABi46DgAAAACXBIWXMAADLAAAAywAEoZFrbAAAQg0lEQVR42uWcWYzrWFrHXTdXaOgZHkComR51Ay8tEBIjNW%2bjEWIQQogHmtGIl%2b4R0CAEvPDSMzwgMVPDI6KFEA9MzwPLcLv7LrXkVlVqr0oqcew4thM7zl6VSi1JHGffncTL%2behjO7lpbi93%2bm5VGUslx6WqJN/v/L/PZ/kfE8RjHrHL8Q18Fi60l4Tz8Y%2bi%2bZGHPx39FXcyfHXyN%2bzJyBU%2bHi2EMirBpAfW75iMSlzrI6MYROxivIBfxwvjV6TLMXc5ADiuA6QUAP50VOVyw3fZk9Frs/8Xyqo3qPTA%2bj86oxJ06hqCSFd065woaTed83cLAwCpMB7FLjVdOB8b4oUB2RoAlxua7PHovXB29Bv/vJyYvgedVl1UUrVBXDcIGXlMpMuG9Vpvw0JS1sO5JkC8qBlSYQyxSw0J52Mzkh/p/OkYMlWA8PFIZ7JDXygz%2bFYgpX5p8l5USr1JJgZEIG5DCCSuOIxMaWyfK7rLPhtvloYASVnTEyUdxYsamoEAkfwI8acjncuNIFbAIIYQyqglKqW%2bTSUHPzd5Xz7XI/zxgVVP/FKPCF2qhD82uILyL2lEpjomztowASGddwHSim4kZQ0cCDADAUXyI1wTEJcbGuzJCCJ5A5JlADqlXmAQAak/BRFIDBb8Ut/ljfWs6yOpf7UAJAsakSlrVuuny9pblz2ATEU3MhUDpRUdORBgBgI4EJADAYWPRyaTHWqRPAKpCEAl1RKZGPyvPz74%2buRzSGm44BP7Lp/QJw4FG4ZXfM4wkhdDIiNrxDY4rS9ruwUMoKzr2YoOmYqBlQCfAAFmlIAhAJMdGqGMqrMnBkTOAKjUCAJx9fAo1v%2b92c/1Rruuw2h3wX7dIQ4i3ecDIHU5JtIl%2b9aXKo1fSpe0ZlYxMQBk/Tw6BHAgICZr1QSTTg8NKqVCJI/rBIKjWH/HJ/S/5RW6L0w%2b/zDadR3wbatOYFXsc61n2PpnIxtCYXzTPmvvlPoA6ZKmZ2QdQ7B/fjIIMAMB0ekholKqQSZUk89jRejgE/u8V%2bj96yHf%2bcrkuxxEOjf32PaN3XCT2OcbxC4LxB7bfLoA4qdDInU5sugnL4evpC7HnWPZhFRRM9MlDaVl7XEgwAwEoFIqIhOqHogPTDpjApcHOIx2eweR7r8c8K1XpnWiDsQu23RtMjXreodrEtuhxtOsAWOr%2bKXOR%2b%2bUOgCpy7GWLmgYAkqXNHgKEFAgPjCOYgPNLw2BOwU4iHTa%2b3z733bZ9u9PvpdwjIjtcMO1Gapb11tM/ckGnjhRiXh%2btOAo4eXk2aidLRqQvBih1OUYpQtjDAGeIASYgQCB%2bAAdxQbIJ/a1o5gK4RzAPt/u7rGtnV22%2bdbsd90K1W9u0bWFDapiXXvo6hOCcDq0u7350TezBROSZyMzdT5GyYsRVgI8RQgwAwHXBPMw2tMPoz2g0ggCCR122aa0zTTe/PdDfmHyfXdC9RsbVOXGBIKHqhCe4OeAIWVUIpFXiXTe6f%2bfqtvnVYBEfqgnz0aQOh/Dk4AQfXQIWAlwGO2hg0hX3%2bfbxpE0gmDKhG2mwW6F6m9v0rXpAMxDVVzrpHJjLVC24KwHlJ8seEv2x6pFMnGs/m6uCJA4HRrJ/AhDQM8BAjhKQFgFB5EOwhD2uJaOQRzFRrDN1GGTrt7aoCpfnY1nLVB23ffLC/c859b1/SP5Ecb7adz69qgtnlX38yWAeG6oJ06HKHk6xBDgOUKYKAHXBLTHtYxdtmlsMw2EU8NDV9FGsPLeOqm8tuYvT7vbbn/p5rL38hEUkOpjFdxw1PCH2XMT4seqmThWUTynosTpEK4OBEsJGALaZZtom2loWAm%2b2Ag26RqsB5T9tUD5DfdR6ecn8a34Cp8cvJiw%2b93xCYD04IdnJQApO9Djxyo4EOAKQcDpADMQcE1AW6G6jgHshFuwz/dgzV8uuo9Kb9/znn3hs%2bWf6jtK6L0QS/Xz6ZwO8YxqStkBciDAFYUAe1wLHCXAVqiONumquRGs6B6qBsE0gPuo9I%2bfGnwk2SOkRN%2b69cWSve%2bcFwFiqYEupQconlGxEuAaQgAbQhUrobx6KP/ix8tf7E5TQIj3vyjG%2b4VUdgxSsm/GUgOQ0gO4ZhBgVglboTqsBZT26pH8qw8FH43aQ00x1nU5578/PQMQ4309luhjCCiW6l9nCOZOuImV0Fgn5VceAiDwXUIQOws2jPYXRbGbzmQNiEk9Q4z3kAMBrjEEc5drwyZVba4H5F9%2bWAFchxCFrlX5RaHzW4LQ1UWxB7FYD8WkHhLjPbjmEMw9voOV0FgPVl/%2baPBs21ZBpGPJX4h23jvNAcxAwEqAzwsheTUgmPuRDlZCdzNU/bWPU4DV%2blG%2b89Uo30FitAui0EWC0EVzAgF3mGAn3DS2mMY3PnrrY9uEwDsAuPatXBYgync0wYaAlQBzAMHqOu%2byLW033PjtafA83SSi4bZd/Jj2a1G2A1G2gwS%2bg7AS5giCNYja59v6Ltv6HSt4jrSnkSKhltXxiTCtt9OSDpFw25iBAHMCwRpOH0S62j7fsafhebJJ8JQNgXRzC3yoxSZFDaLhthEJtxFWg8B3YE4gIBvCAKfD60TY35ikgFX5ear5ZlZCwIdaeoRpo2i4jSLhNswRBDypYk22Hka7f0Gw7waJCN0iKNbuAXLBphSPDCFCtww%2b1AIHAswRBDSZbfaJ/T8juGAP1wCXXQuabyUjY%2bCCTYOnWihCt5ADAeYIAp5oNRl78eXPrRQAZ6mL9Td2UxEdeLKpc8Em8FQLKwHmDAJefDHDJwj88f6fEuxR3br1sd7aS%2bxRo8mTLeACTcSTTTSnEPC6g4FXnshE/y8J1lu3bn1hb/2dDG8Cd9TQOX8TQ8BKgDmFoKUqeOlNXbSlf1h/hfXWO7y/DayvYXJHDcT6G/MKAa9Fati18mFNsAEwB7V3MqwBrLeusb4GhoC4owbMKQS8Kq1l64CVsEiEdisvM/vVNudrQviwjlhvHYW9dQwB5hiCdtwAnA4/IEK71dcj3jYw%2b1UzfFBD4cM6VgLMOYRxrgXAnoy%2bRzA7VW/MrwKzVzPC%2b1UIH9TgpwCChv2MXG74H0Rou5KKHLYhtFM1mb0aVsIVhTByIIwgeTF%2bXAg6BsDnRj8m6E3lj6KHHWB2qmZop4qYvRpirrwSHhuCjn2N0fzov23X5mYlKPr6GIIR2qnCTwEEPd8GrAQHgEf5ZuSgA6HtqsHsVJGjhCuWDsMnmQ76WQdAvBj/5wPv7qZCir7BBALMOQQLQOxyfAe3vstRwevsTgPorYoR2q4gRwkwpxCM05blbfYT9LpMhLZsKwntUW6lSA1D0ELbVZhjCAauAYmS5p3UgAmA36Q9Sje8XcMQUGi7Op9KqBoG9jcnZc2Hg7Y3MngUa1RIbSjfl3xDCG1W9NBWFZx0gDmDYFz2LYP3wUQBRHDDNhEFNuQvUxuKzO00MQTTVkIF5gyCedbGJm9DsDcteGxPHbVuF0RqXVkUDwdAeyp6aLMC8wYhXdbMXB0go%2bgX9lT4RpmI77WI4LqtAnJdfpFaV2rsdgNDMB0IMEcQJgDy034AhhBYKuNaYBVEaq38d5HdDlAbikF7Kii0WUFzBMHM1QAysnb20OIo6S4TALZ/jl4rJ6J7UwgwPxDG5kkVsBLyDwWPj%2bD9sqMC5Q%2botTKi1xUMAdEeBc1JOpgnFQSp0vhhsyC9rhCBVZlgPJUFB8aquN8Hel3RqQ0FnHS4zhAcg7flcjcfAkCt2f2CoNtWQdBd/hq9VgFqTcFKQLYSrHS4bhCwrRclzy2HO1aCfqI4CyIfVweC7hJBu2u2CtzyqrDbwxB0BwI8awgWgM8PAdt6kaMEM3k%2bGhfbeL/DSPhUr2BwtWSrYFX%2bemitCsH7ZeTUhGcOIfr5ICALwoll6zWTp0M9c2lAoQU4HWKJ89Grnxg8db9k1wS3PIFwK7Y3wBA0ak2BZw1BeHQIyDFzonhWnXib9cy5ARdVy%2bkuJ/LDH0j5/pc%2btfWnd4TVKYCvBFflPrNuKcF0agJcMQjI9jFaZk4znlH11KkGZzJgEEr8RF1M5Ppfnm4CObf3QH0yhFXZgVC2BkrkSvkfxJ0%2bUO6yTt1X4ApBQA4E7GM0pWRfTx1rkC8ASJmBImUGi1K6%2b%2bKDHXBDV8LZBfeZB%2bUuE%2bSSnQ7%2bW2c/Q67IKc7TxBCM4P0yOOnwPCDYzrUH7jUzJvX0ZGYE%2bQuAWLIvf1gTFqV0bxp4PKe6Ejl778NltUXET4afDYBcKRGBu6dEcEW2BkrkculvI1tdCK6WDcpdRnZhfOYQbN%2bSrQRTFLp6IjGE01MAUeopH6bDopDoTqUuZVWXlO5ZgccyfSKRHTxa8LNH4J49cArcyf8suVLKhDeaEFyVTcpdhmcIwbbrcBYAU%2bA7elwawsmJZeZURLG7KEY70xaX0gOXlO4vSOmOc937fDvGyCV7ZwW5XHJUUPwbYasH5IqsB1dl5CjhaaXDxKmCHAhmJNzWJWEAJxnLxyhHI51FUWhNA4/Fey4xYbd4/lIjhHjv8bfNBe4VCHKpaE%2ba3D1/gVwuSeH1OoZgBFfL8JQgYJMGcpRgYuNWjOtDNoFwOigRrr0Y5ZpTqcdiHZcg2JusBbFDxGL9JxO80%2br2HWHJUcGS/I2Ip40BmOSKjBwI8IQgTPwJ2KlicsGmLrJ9yEgGTgeFZ1qLXKj54gOLf8clCp2FqGA/cEEQntLu8uByifDflQluo%2bikRsnNb7QsFTgQ0GNAmCzNIweCyfobukB3ISMYOB1knmou8uQDqUe5tivK2%2b7WkIQI4WnvJp/UgsC9ov2oi7uFV8mlkkqtKBgCegwloJmleTPsretRsgMpTsPpoHCBxiJPNqZSjzBtF8e0rMB5pkVEwh2Ce1Zb6Sd9gsCSfVsM3Cv%2bUNjsQXBZ1oMrMjw6hI%2bsO6Cw7U/Qo/4OJMNjnA5K2Fdf5Ly1aYvzVNPFU60FlrGD5ehn%2bPyA2cN/B/cNbBUEbhd%2bPXCv1KeWyxiC6SgBPgXCZHoNORDwgqwR9XUhQY%2bAOaiVmYP6Ymi/Og2cCzRdHNm0WlxiywRHPqfAJ8fR/TIR/K/8AxXcLb4rbvaBXCppwWUZPh5CeWYAZc0sGfRWRRe9PRB9PZwOp8xe9Z%2bY/covTQP3NVxhnz0kZ311y9PIkbXn/yAV8rZTC24X7NviB4VfCdwtluiVCoZgOhBgBsLkFono9bJBbSh69KALkk/F6SAy29VvSwFq%2bv7hw5qLOawv0H472JD3CgT9iRDuFG/aaVH8TmxLhcC9kkYulXA6oP9XGPHYwYjstCF2MMDpINAe5Y37a3E7yK0GEd6v3WD2q/YzSgIFIrR/BQOfPbhlhfA7II4%2buPiC/04xHHY3MASDXJInEPAtUuc32yDs9IC6X5bodeVN7/eT0/dhtis3mYMaNmwRoe0qwexUrn7wTuvbRfF20WVDKPwx625C4G5pbEMo6bifEMWDpxVZDLrlb39kAtajuOjtqqMAhaC3qsS1OzAE7/sForxvP8XF/0FhN7WrQ3i1DtGNLq4JQnBZfsPzY7fd2u4aQa2XXXj2eXYS9toevkkKvG8XRPL94i/4bxf%2bOnCn%2bCPybvFPlv4nOn2sRdAt3wxsOf2I1RJeg3zu3///AIiGBwrvbjiXAAAAAElFTkSuQmCC' /%3e%3c/svg%3e) Application-level Consensus
Application-level Consensus
- Shared-state attestation management based on digital certificates allows you to integrate cryptographically verifiable checkpoints of the states between multiple actors. “What you see is what I see, I know you see what I see, and I know that you know what I see is what you see.”
Crossing the chasm is as easy as one, two, three.
Keychain Core packages powerful security concepts so that the common IT team can confidently deploy next generation Web3 applications.
- Download and install.
- Download the Keychain Core package and clone one of the Keychain solution accelerator projects. All Keychain Core dependencies are baked into the package for you.
- Build.
- Our solution accelerator sample code repos include build-ready projects for all environments (Windows, Linux, Android, Apple). You’ll have a working demo running in minutes!
- Go!
- Use the templates from the solution accelerators as a springboard for your own projects or create new projects from scratch.
- Independence and control.
- Keychain Core is built from the ground up to minimize the areas you must entrust to a third party, even Keychain. Further, Keychain Core is designed to be minimally opinionated to give you maximal control over decisions such as where to store data and what infrastructure to use. We don’t not see your data and keys, and lock-in is minimized using standard formats.
- Interoperability.
- Keychain Core is the first framework that combines Web3 capabilities and out-of-the-box conformance with established international data security standards. As Keychain and other partners deploy end-user applications, your applications will be, in principle, interoperable with them also.
- Agility.
- With native SDK, command-line interface, and API touchpoints, Keychain Core readily integrates into existing and new applications, on-prem and hosted environments, and online and offline scenarios. This affords you the freedom to separate data security concerns from IT architecture.
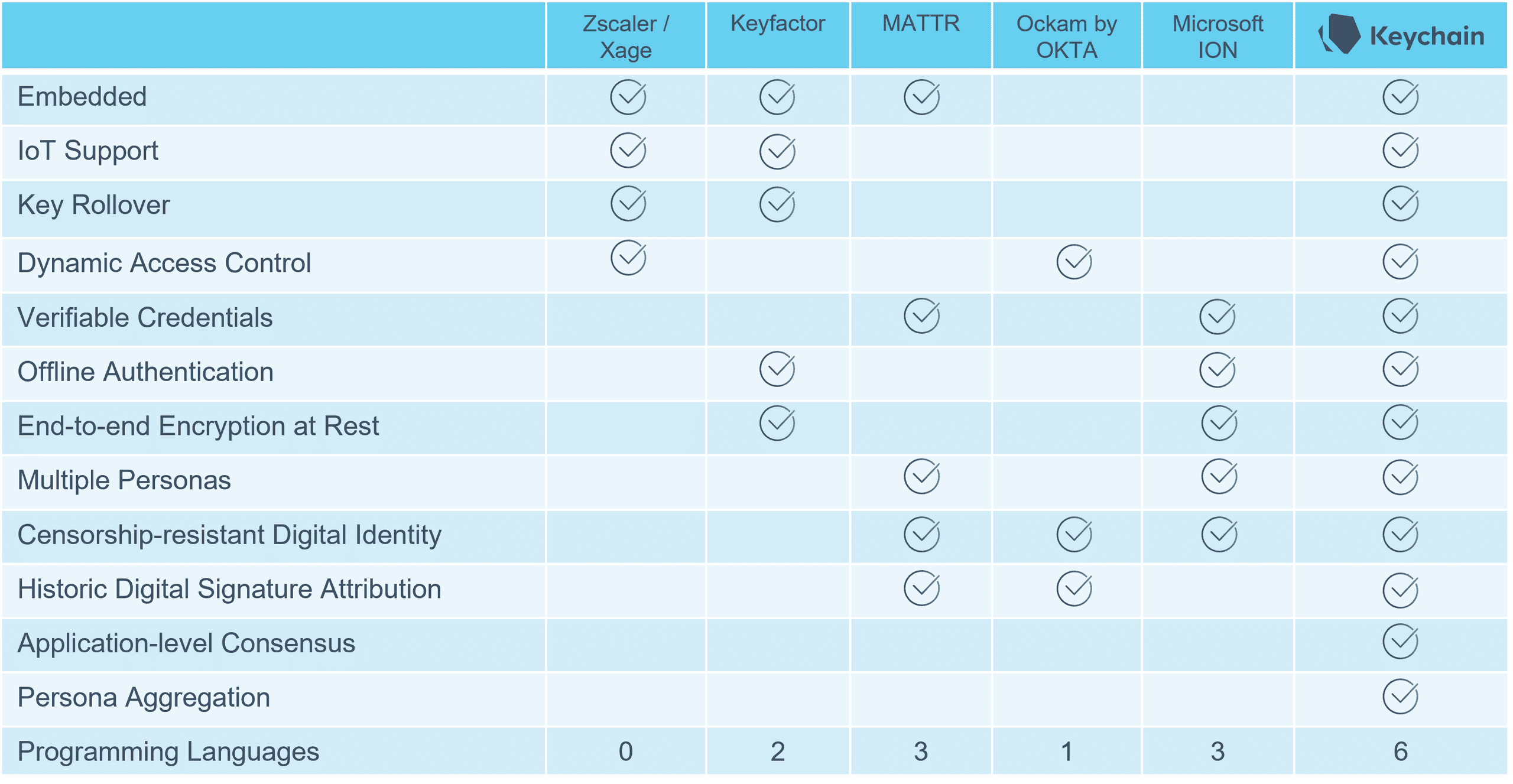
Keychain is the most comprehensive Zero Trust framework available.
Whereas most vendors cut corners to get to market faster, Keychain did the work to provide you with the most comprehensive, one-stop, decentralized framework available. Great team leads demand the best tools available for their teams.
We’ve done the hard part, so you don’t have to.
Remember the good old days when managing data security and digital certificates across a diverse range of devices was easy and fun?
Ya, neither do we.
- Capabilities
- Self-sovereign digital identity, end-to-end data encryption at-rest & in-flight, signing / verifying data, verifiable credentials, key rollover, historical digital signature attribution, application-level consensus
- Devices
- Servers, desktop, laptop, tablet, smartphone, smartwatch, smart glasses/goggles, IoT gateways and other small devices
- Operating Systems
- Android, Windows, Mac OS / iOS, Linux
- Languages
- C, C++, Java, C#.NET, Objective-C, Python, SWIFT, (Golang forthcoming)
- Supported CPU Architectures
- x86, x64, ARM (v6, v7, v8, v9), M1, RISC V
- Required Device RAM
- 64 MB
- Keychain Core SDK Size
- 16 MB. Megabytes, not gigabytes. Hermetically packaged (dependencies and database included)
- Cryptosystems
- AES-GCM, DSA, Camelia-GCM, ECDSA-ECP, RSA-OAEP-SHA, ECGDSA-ECP, ECIES-ECP, RSA-SS, DLIES
- Conformance
- ISO/IEC 18033-2, SECG SEC-1, ISO/IEC 18033-3, FIPS-186, ANSI X9.63, NIST, ANSI X9.44, CRYPTOREC, IEEE 1363a, BSI, IEEE P1363, ECRYPT
- Public-Key Infrastructures
- Conventional PKI, Bitcoin blockchain (EVM-compatible blockchains forthcoming)
Keychain Core plans
Choose the plan that's right for your application.
Explorer Plan
The essentials for desktop applications.
Contact us- Linux x64, Windows x64, Macos x64, M1
- Test environment hosting (for test nets, faucets, communications servers)
- Desktop solution-accelerator sample projects (source code)
- Software maintenance support
Innovator Plan
Everything in the Explorer plan, plus mobile device support.
Contact us- Linux x64, Windows x64, Macos x64, M1
- Android x86, x64, armv7, armv8, armv9
- iOS armv7, armv8, armv9
- Test environment hosting (for test nets, faucets, communications servers)
- Desktop and mobile solution-accelerator sample projects (source code)
- Software maintenance support
Trailblazer Plan
Most popular
Everything in the Innovator plan, plus IoT device support.
Contact us- Linux x64, Windows x64, Macos x64, M1
- Android x86, x64, armv7, armv8, armv9
- iOS armv7, armv8, armv9
- Android WearOS armv7, armv8, armv9,
- Linux x86, armv6, armv7, armv8, armv9 (and any other requests)
- Test environment hosting (for test nets, faucets, communications servers)
- Desktop, mobile, and IoT solution-accelerator sample projects (source code)
- Early access to pre-release builds
- Premium support
Frequently asked questions
Have a different question and can’t find the answer you’re looking for? Reach out to our support team by contacting us and we’ll get back to you as soon as we can.
- Is Keychain a blockchain?
- Keychain is not a blockchain. Keychain Core is a layer-2 software framework that you integrate into your applications/systems and that acts as an extension of your application, providing capabilities related to key management, data security, PKI/blockchain interaction, and off-chain DLT consensus.
- If Keychain isn't a blockchain, then why is it called Keychain?
- Over the lifespan of a device, the device generates a sequence of public/private key pairs that defines one of its cryptographic identities. Keychain software provides you a systematic way for generating, publishing, and tracking these sequences of keys. Hence the name.
- Where’s your white paper?
- Cypherpunks write code.
- I work for a technology development consultancy. Can we use Keychain Core in our solutions?
- Absolutely. Apply to our reseller partnership. You’ll be more efficient at building solutions for your clients.
- For whom are Keychain products built?
- Keychain is not for everyone. But if you're an innovator focused on creating seamlessly digital experiences and operational processes with the best security tools, Keychain might be for you. Contact us.

 Self-sovereign Identity
Self-sovereign Identity
 Data Security
Data Security
 Verifiable Credentials
Verifiable Credentials
 Application-level Consensus
Application-level Consensus